-
Smart-Contract-Vulnerabilities-DB
-
Base Sample
-
Images
-
LICENSE
-
README.md
-
run_on_database.sh
Smart-Contract-Vulnerabilities-DB
This repository is a sample of the developed database implemented for the final paper of Ryan Weege Achjian, from the University of São Paulo (USP). The reason for sharing only a bit of the developed database is to ensure that it remains private until the publishing of Ryan's master thesis.
Executing a Vulnerability Detection Tool in the Database
In order to run a vulnerability detection tool in this sample base just clone all the files to a choosen directory and run the following command line:
./run_on_database -c "det. tool call %sc" -o output/directory
For more information on how to use the bash script, just type:
./run_on_database -h
Database Characteristics
The full database that will be presented is comprised of 112 vulnerable smart contract from one of the following vulnerabilities:
- Call to Uknown
- Costly Pattern
- Gasless Send
- Hash Collision
- Mishandled Exception
- Overflow and Underflow
- Reentrancy
- Selfdestruct
- tx.origin
- Weak Random
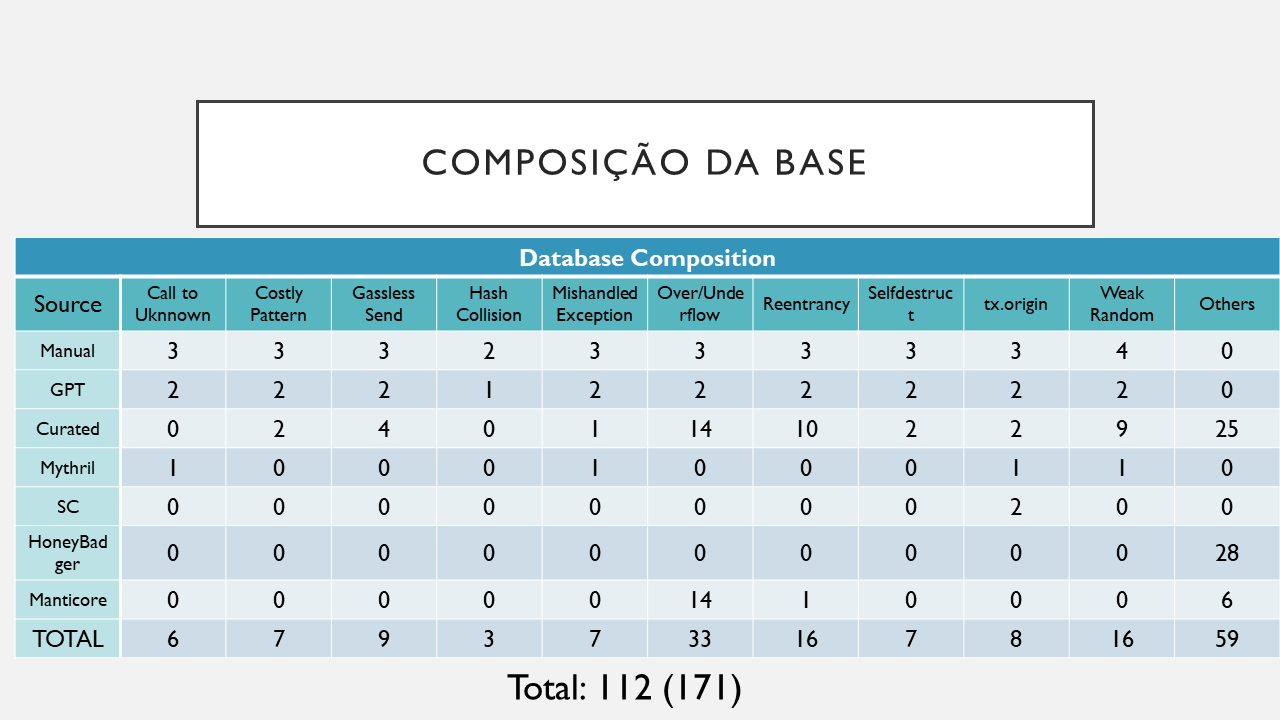
Another 59 vulnerable smart contracts that have different kinds of vulnerabilities where compiled in the database as others.
Database Implementation
Fifty vulnerable smart contracts were implemented and labeled a prior, that is, a vulnerability was selected and then a smart contract implementing an application that could be affected by the choosen vulnerability was selected. The implementation was done mannualy a via generative AI in order to have more variability in the database.
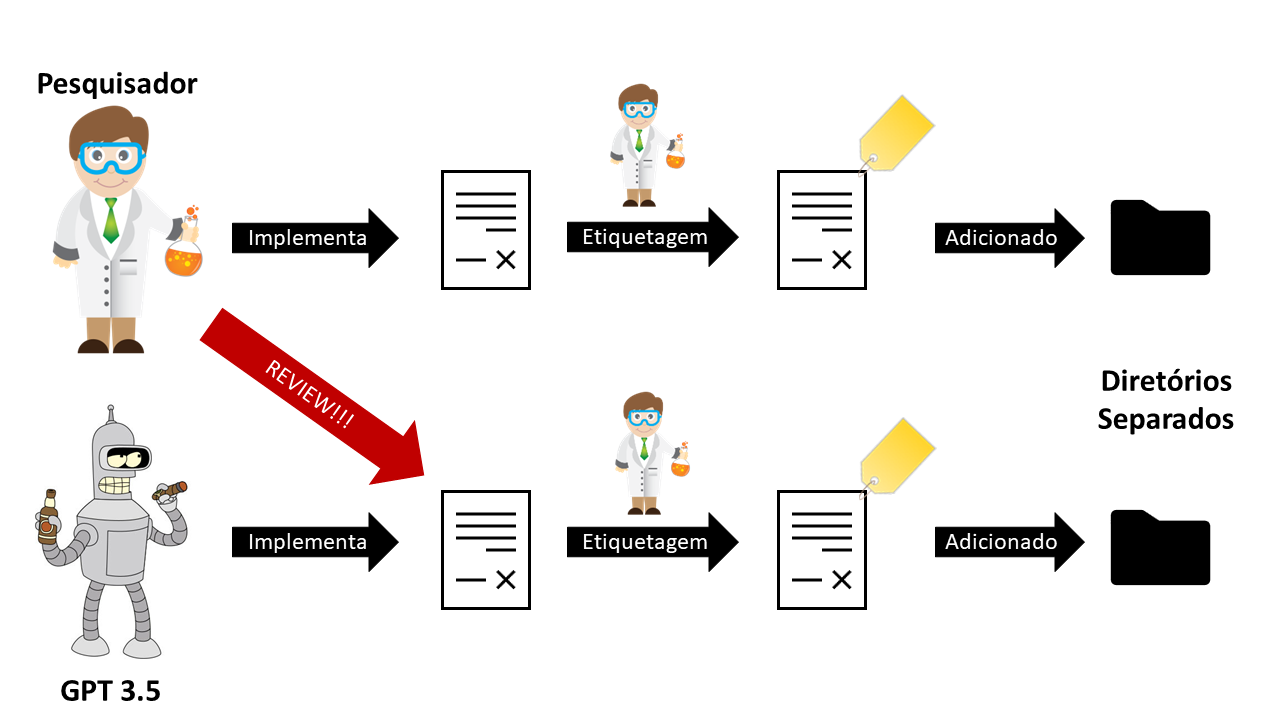
Before the manual and generative AI implementation, other vulnerable smart contracts from external sources were added to the database. The inclusion critiari was that the external database had labeled, vulnerable smart contracts that had the same characterustics as the smart contracts implemented.

Tests
Following the database implementation process two vulnerability detection tool desgined to point out bugs in smart contracts were selected to be run in the database. The selected tools were SmartCheck SmartCheck and Mythril Mythril. The first is a static detection tool that, despite supporting only up to SOidity 0.6.0, is simple and lightweight. Mythril is an open source dynamic vulnerability detection tool part of the vulnerability detection suite developed by ConsenSys and constantly updated by the community. The results obtained pointed that none of the two tested vulnerability detection tools were able to reach a detection rate above 50%.
